Could the Alliance breach have been avoided?

Nov 14, 2025

Samet Gökbayrak
Could the Alliance breach have been avoided?
Quick answer: Yes.
Another cyberattack on the Allianz Group: After the incident at its U.S. subsidiary Allianz Life, in which data from 1.5 million customers was compromised, a British subsidiary has now also been affected.
What happened
The ransomware group Clop is currently exploiting the Oracle security vulnerability (CVE-2025-61882) for large-scale cyberattacks. Victims so far include, among others, The Washington Post and a subsidiary of American Airlines. Most recently, a British Allianz subsidiary was also affected, resulting in a data leak impacting hundreds of customers (source).
The incident at the British Allianz subsidiary became known on November 10; more than a month after ENTRYZERO had already flagged the vulnerability as significant for hackers and warned that any affected organization should act immediately.
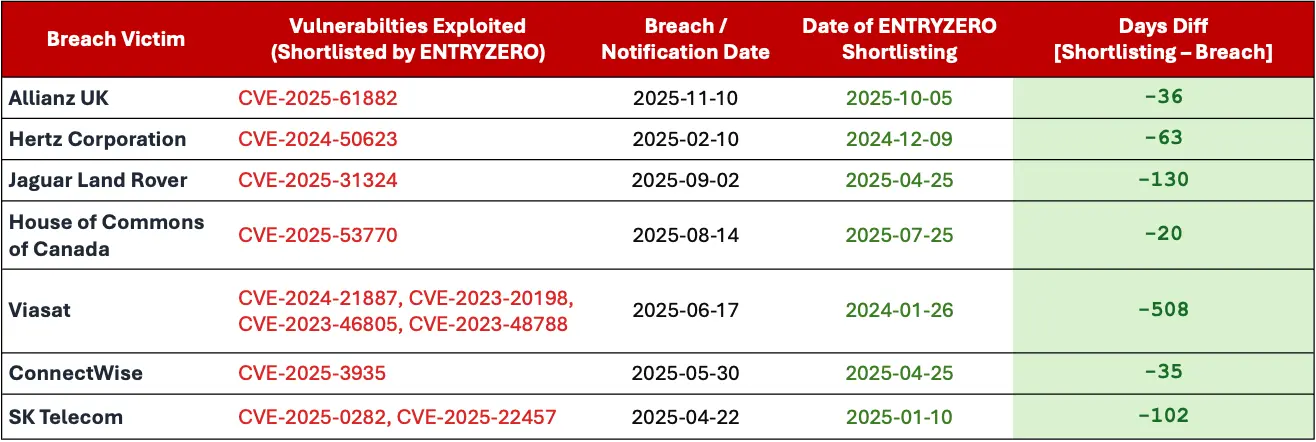
How to prioritize differently
ENTRYZERO developed a decision-tree-based prioritization approach, trained on over 100,000 vulnerability and threat data points.
It extends industry standards like CVSS and EPSS to better capture real-time risk and contextual relevance of new vulnerabilities. The following table highlights ENTRYZERO’s capabilities in vulnerability intelligence. It once again shows — also in this Allianz case — that ENTRYZERO prioritized the issue faster than the U.S. CISA.
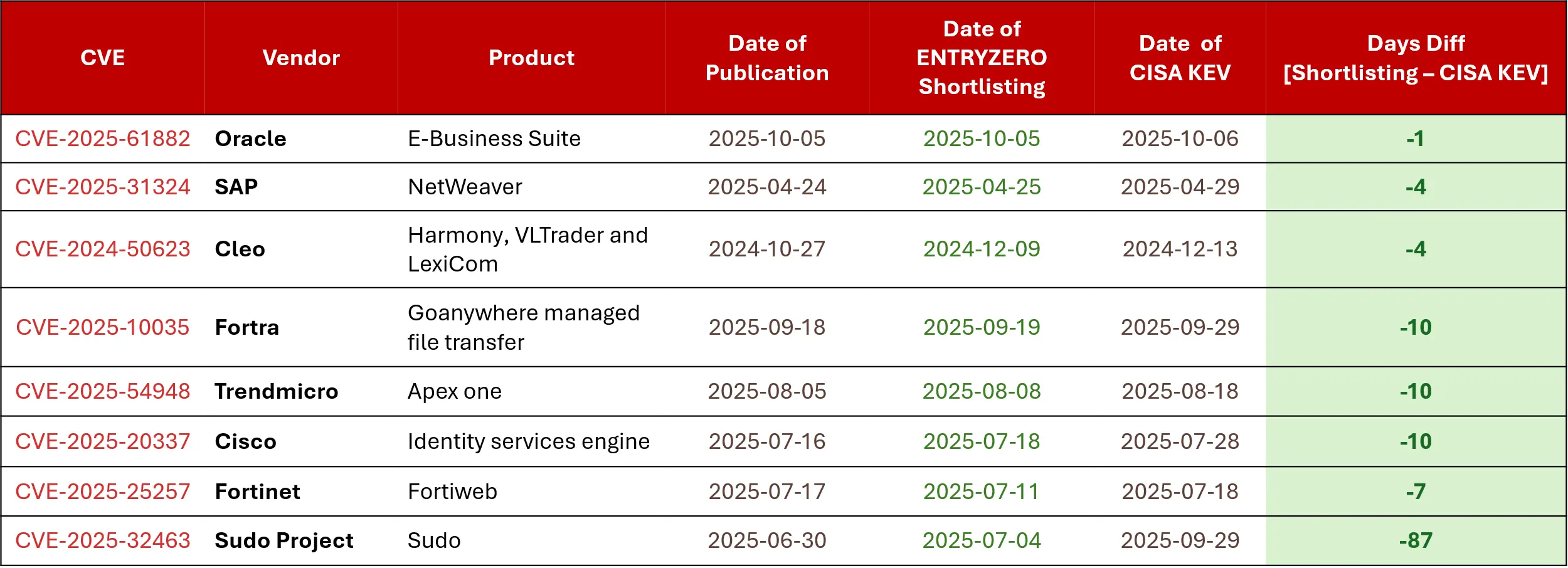
How to take a preventive approach
- Ensure maximum transparency of your attack surface across all subsidiaries
- Identify exploitable vulnerabilities and deprioritize those posing no real risk
- Run the above two points continuously to stay ahead of the evolving threat landscape
In a nutshell, adopting a risk-aware approach to vulnerability prioritization is the way forward.