Im Schatten der Angreifer: Die Bedrohungslandschaft Deutschlands

10.12.2024

ENTRYZERO
Die Cybersicherheit in Deutschland entwickelt sich ständig weiter, während verschiedene Advanced Persistent Threat (APT)-Gruppen kontinuierlich die Abwehrmechanismen des Landes auf die Probe stellen. Dieser Blog nutzt Daten des Bundesamts für Sicherheit in der Informationstechnik (BSI), der Malware Information Sharing Platform Galaxy (MISP Galaxy) und von MITRE Adversarial Tactics, Techniques, and Common Knowledge (MITRE ATT&CK), um eine zentrale Frage zu beantworten: Welche APT-Gruppen nehmen Deutschland ins Visier, was sind ihre Motive, und welche Methoden setzen sie ein?
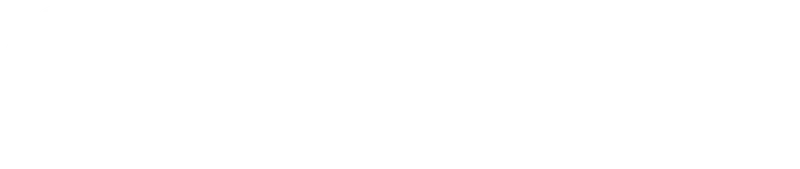
Predominant Threat Actors Targeting Germany
The available data indicates that a majority of the APT groups targeting Germany have been attributed to China and Russia. These groups primarily pursue strategic objectives, like espionage or sabotage, making it crucial for organizations to understand their risk profiles. This blog looks at 44 such groups that have been reported as being active in Germany.
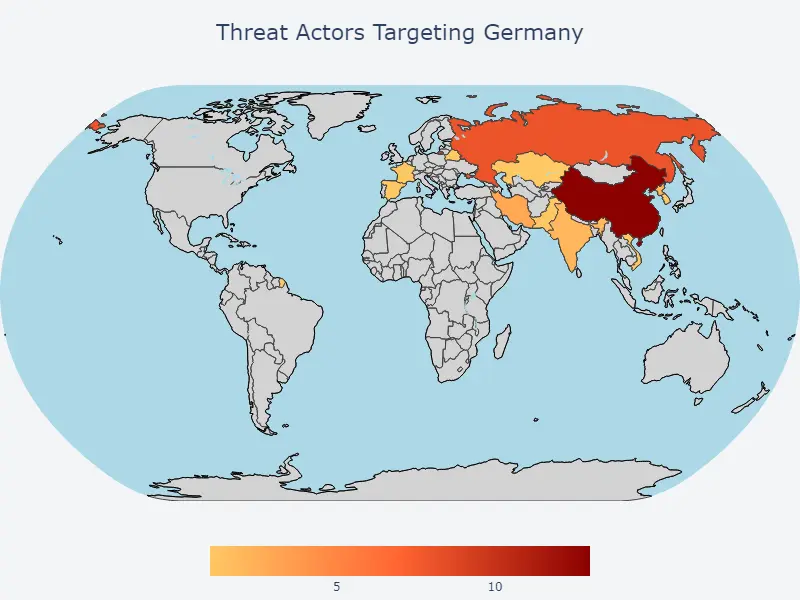
22 out of the 44 threat actors were assessed as engaging in espionage or sabotage activities, while the motive was unassigned for the remaining 22.
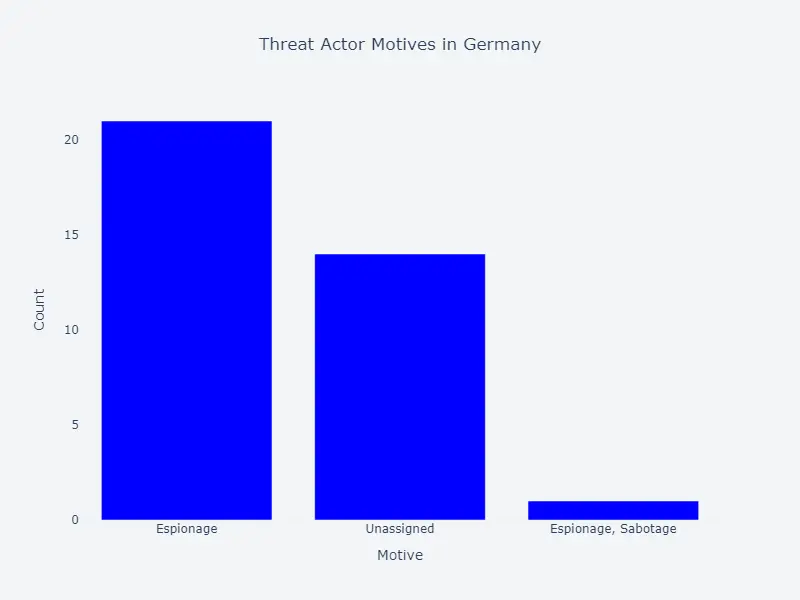
Targeted Sectors and Industries
The sectors most frequently targeted by these threat actors include:
- Government (General)
- Private Sector (General)
- Civil Society
- Military
- Education
- Telecommunications
- Medical
Collectively, these seven sectors account for 70% of the activity.
Distribution of ATT&CK Tactics
The following plot shows the distribution of ATT&CK tactics used by the threat actors, with Defense Evasion being the most widely used.
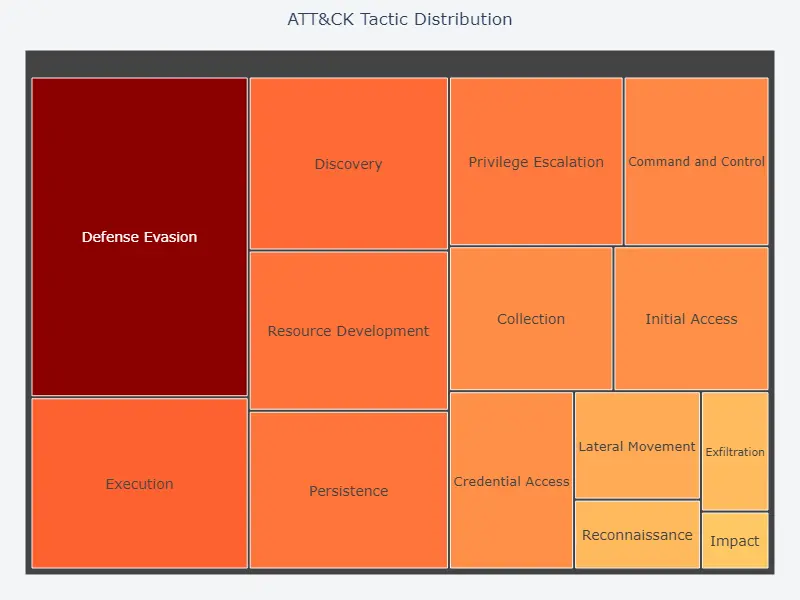
Given this tactic distribution, the five most popular techniques employed by the threat actors are: Spearphishing Links, Obfuscated Information, Malicious Links, Ingress Tool Transfer, and Domains. Looking specifically at Initial Access, the most prevalent techniques are Spearphishing Links, Exploit Public-Facing Application, Compromise Software Supply Chain, Drive-by Compromise, Spearphishing Attachment, and Spearphishing via Service.
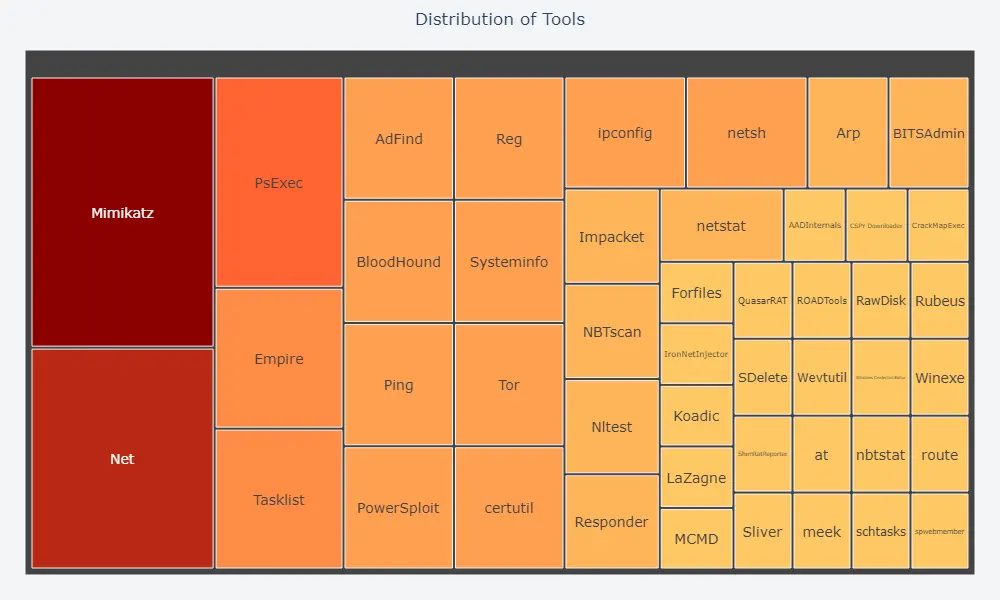
Tools Utilized by Threat Actors
Threat actors utilize a variety of tools to support their operations. In addition to Cobalt Strike, the most popular tools include Mimikatz, .NET, PsExec, Tasklist, and Empire.
Conclusion
Sophisticated threat actors employing diverse tactics, techniques, and tools continually challenge Germany’s cybersecurity landscape. By leveraging insights from BSI, MISP Galaxy, and MITRE ATT&CK, we aim to empower organizations to better understand these threats, optimize their resources, and strengthen their defensive posture.