Could Hertz have been warned months earlier with a better supplier risk management?

Oct 16, 2025

Samet Gökbayrak
Could Hertz have been warned months earlier with a better supplier risk management?
Quick answer: Yes.
Over 60 organizations were impacted through a single supplier breach at Cleo, exposing data from more than 3,000 Hertz customers alone. The Hertz Corporation was not informed until February 10, 2025, months after the vulnerability was exploitable (source).
What happened
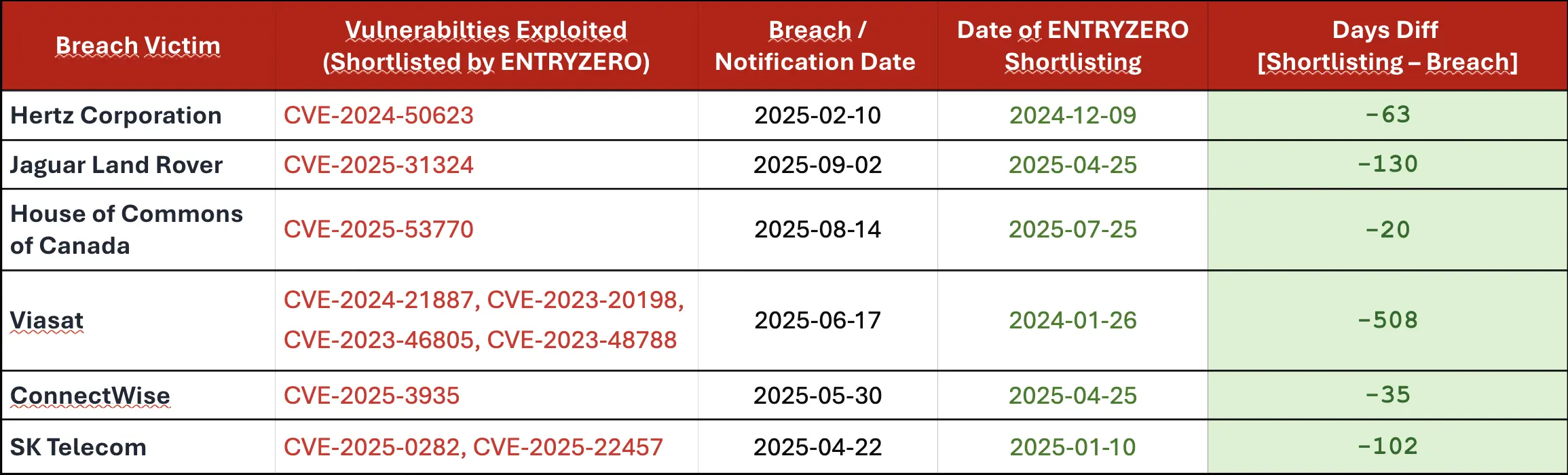
The Clop ransomware gang exploited a vulnerability (CVE-2024-50623) in Cleo’s managed file transfer software. One vulnerability in a supplier’s system (Cleo) that severely impacted dozens of organizations, including Hertz. ENTRYZERO had flagged this CVE as an “Act Immediate” vulnerability months before Hertz’s press release about the supplier breach. With proactive supplier monitoring, Hertz could have identified the risk earlier and implemented protective measures.
How to prioritize differently
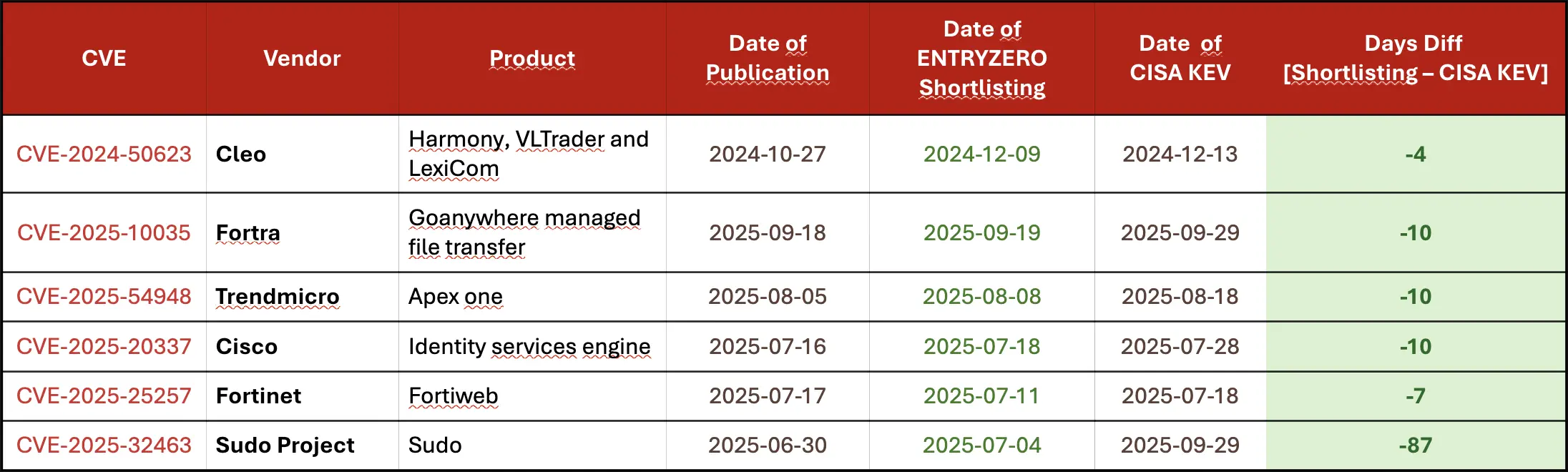
ENTRYZERO developed a decision-tree-based prioritization approach, trained on over 100,000 vulnerability and threat data points. It extends industry standards like CVSS and EPSS to better capture real-time risk and contextual relevance of new vulnerabilities. The following table highlights ENTRYZERO’s capabilities in vulnerability intelligence. It shows that CVEs were shortlisted before they were added to CISA’s Known Exploited Vulnerability (KEV) catalog.
How to increase supply chain resilience
- Ensure full transparency across your supply chain exposed infrastructure
- Assess vulnerabilities from an attacker’s perspective
- Empower your suppliers to proactively mitigate risks before they strike
To this end, a Threat-Informed Exposure Management solution can be highly valuable. Such a solution enables you to:
- Act proactively to prevent data breaches and business disruptions
- Incorporate concrete security requirements and and response procedures into supplier contracts
- Make informed decisions about supplier relationships
In a nutshell, your suppliers’ weaknesses are your risks. Continuous monitoring of your supply chain is crucial for modern cyber risk management.