Black Basta: Profiling Threat Actors in the German Landscape

Mar 5, 2025

Abhilash Hota
A recently leaked chat log from the threat actor Black Basta offers a rare glimpse into the shadowy world of cybercrime in Germany. Our analysis reveals how threat actors discuss security vulnerabilities in their internal chats— which weaknesses they target most, what attack vectors they use, and which products are in their crosshairs. We examined 51 vulnerabilities mentioned in these conversations in connection with German domains. The findings paint an alarming picture of the current threat landscape and highlight the urgency for proper prioritization of vulnerabilities for remediation.
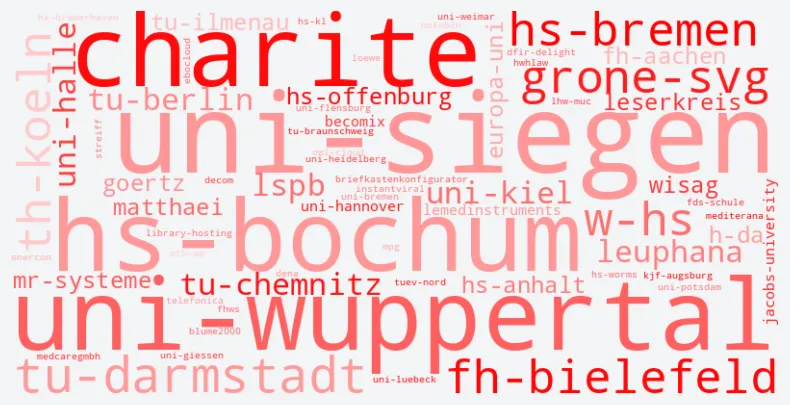
Victim German Domains
This wordcloud showcases German domains targeted by the threat actor black basta.
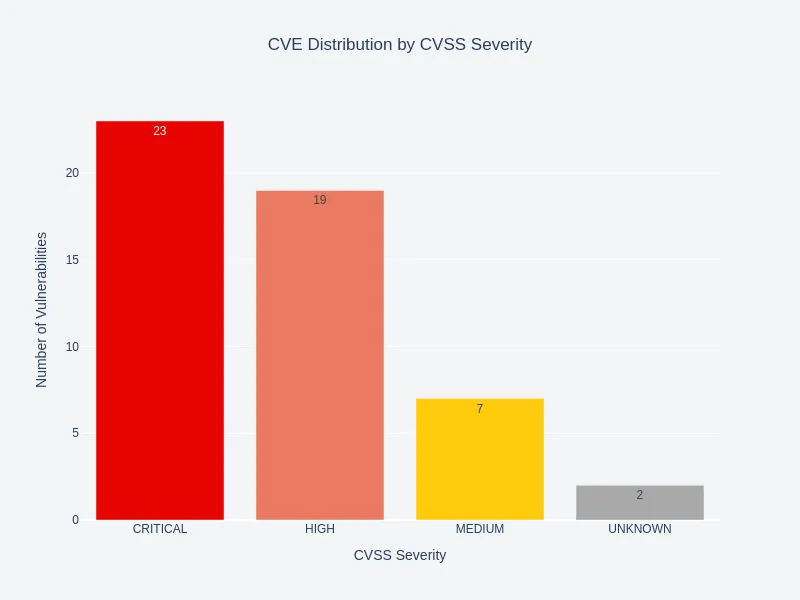
Exploited Vulnerability Severity Distribution
Vulnerabilities with “Critical” severity account for less than 50% of the exploited ones, highlighting the limitations of a purely CVSS-centric approach to vulnerability prioritization.
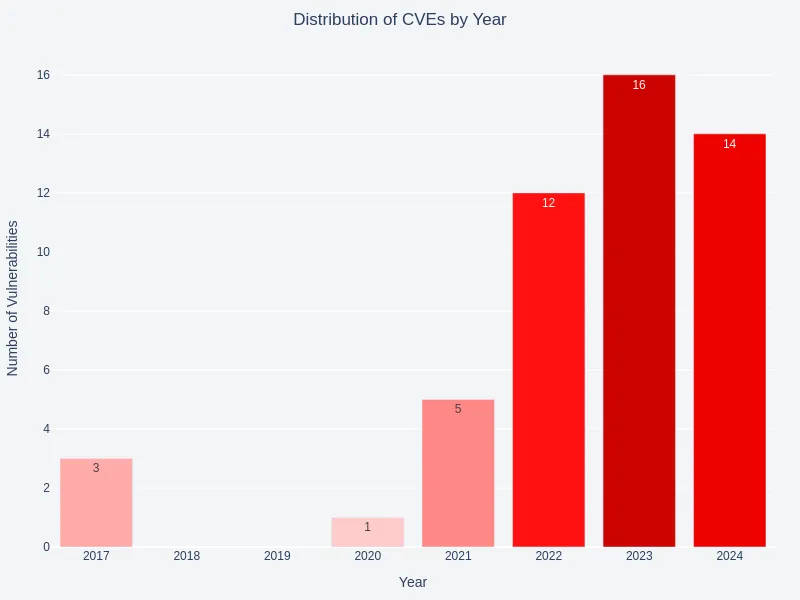
Exploited Vulnerability Age
Analysis by year indicated a focus on newer vulnerabilities, with most vulnerabilities (CVEs) published between 2022 and 2024.
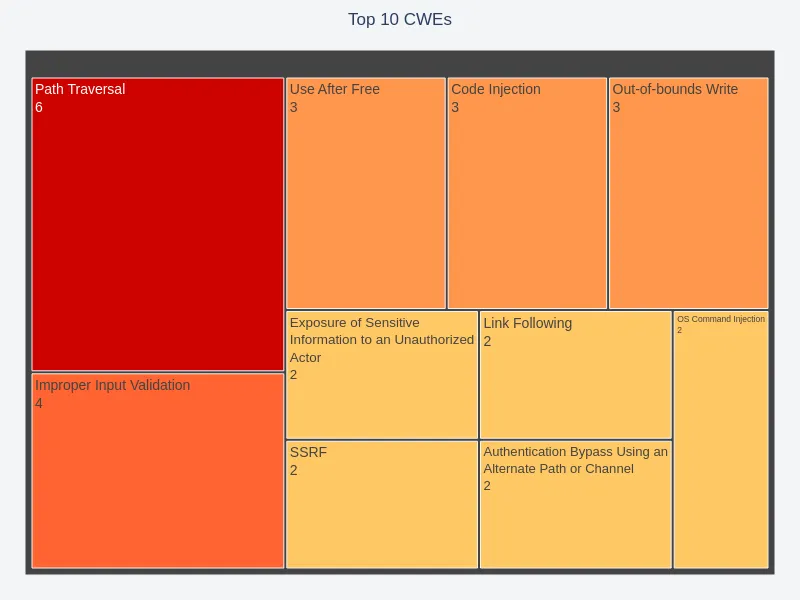
Common Weakness Distribution
The top weaknesses, as identified by CWE IDs, pointed to common risk areas. Path traversal, improper input validation, and memory safety vulnerabilities are the top 3 in these chat logs.
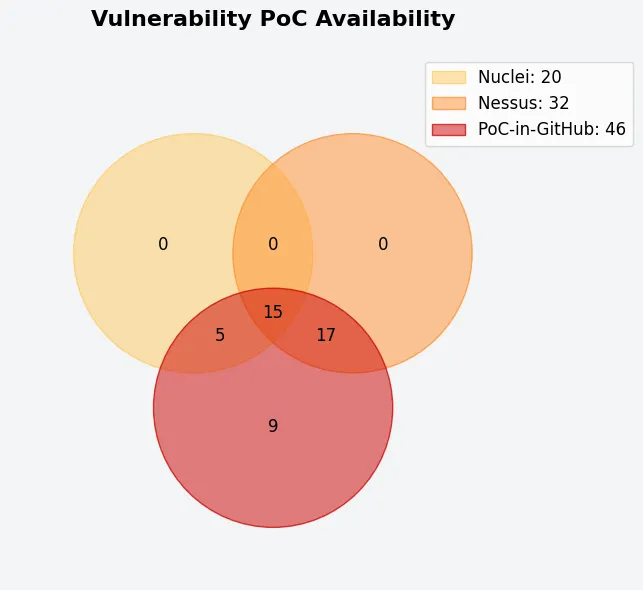
Availability of Exploit Code
A PoC (Proof-of-Concept) source analysis revealed the easy availability of public and commercial exploit code for the vulnerabilities. It overlaps among scanning tools and PoC sources.
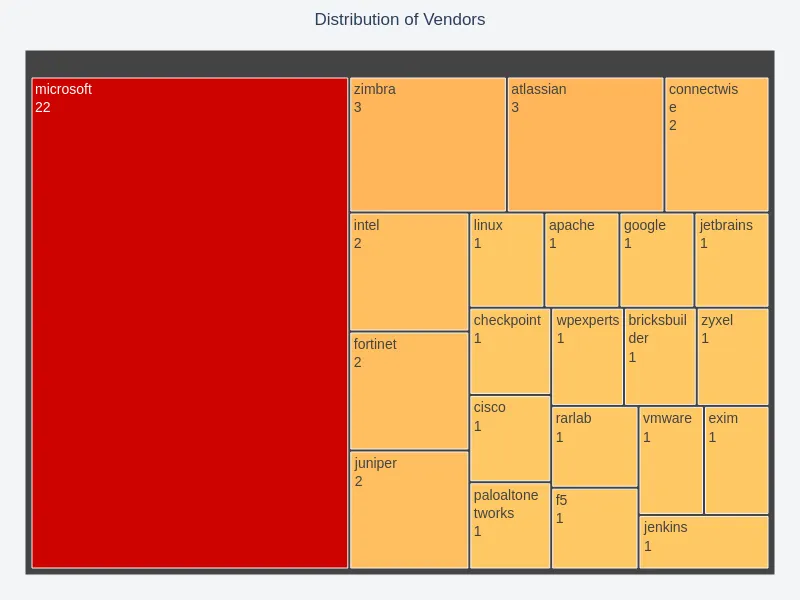
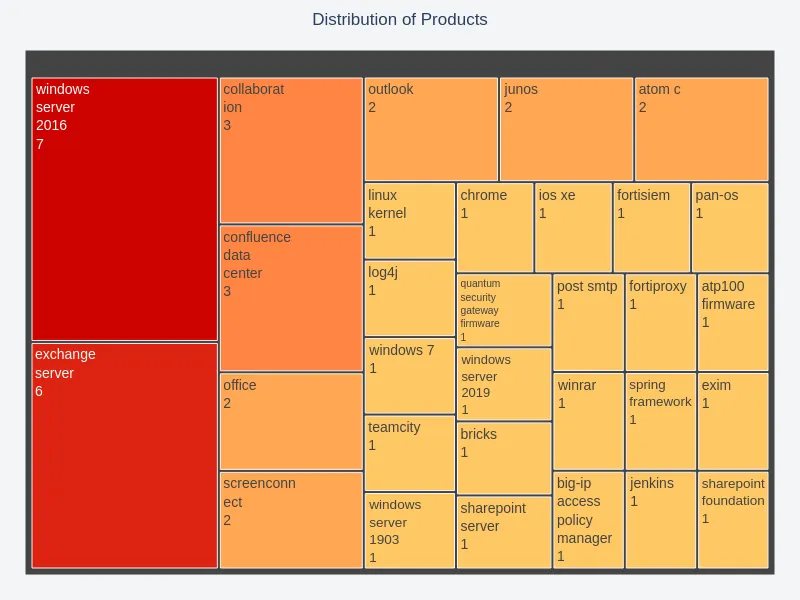
Exploited Vendors and Products
Certain vendors and products consistently dominated the conversation. This insight may help stakeholders prioritize which entities to scrutinize for potential vulnerabilities or targeted interventions.
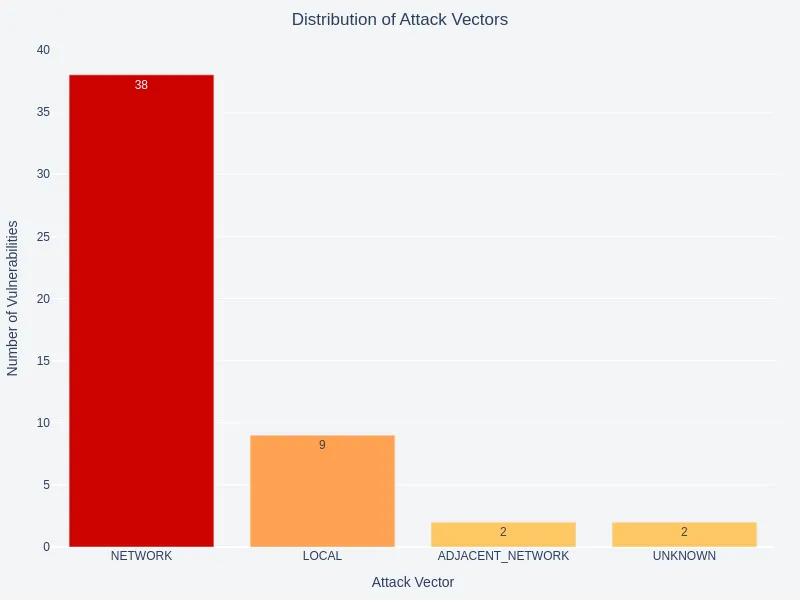
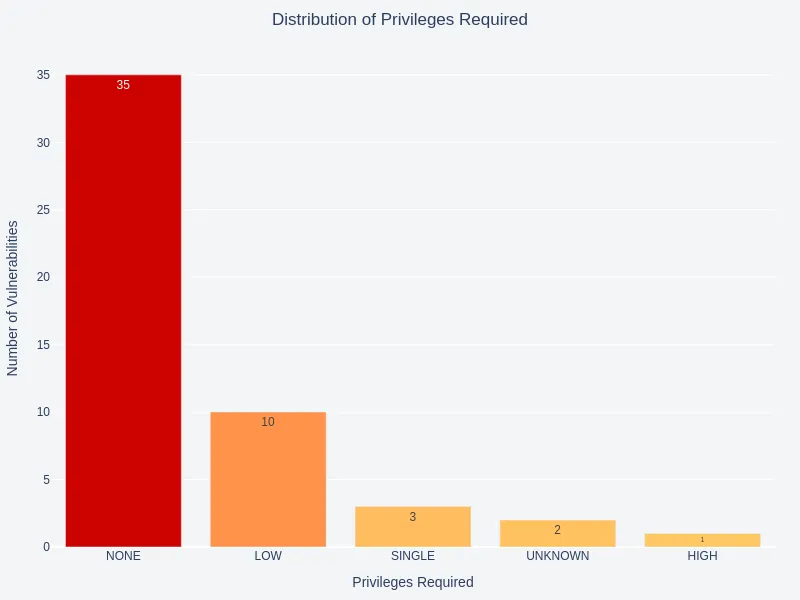
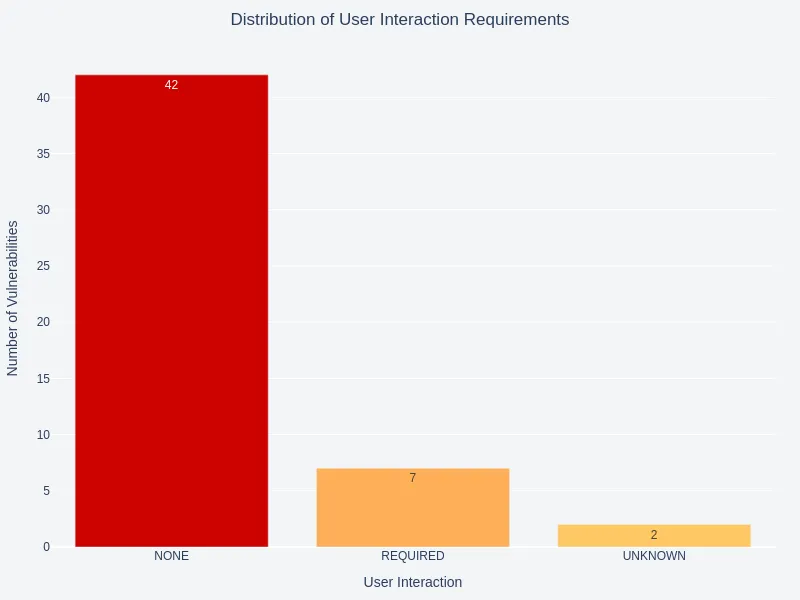
Exploitability Metrics
An analysis of attack vector and privilege requirement distributions reveals a significant focus on unauthenticated, remote attacks. Most vulnerabilities mentioned in these logs require no user interaction.
Conclusion
These results offer a snapshot of an attacker’s view of the cybersecurity landscape as captured through the leaked Black Basta chat logs and underscore the importance of a threat-informed approach to vulnerability prioritization, considering various factors, including exploitation, age, and product importance, among others.
We recommend adopting more nuanced, context-sensitive approaches like the Stakeholder-Specific Vulnerability Categorization (SSVC) introduced by CISA. SSVC proposes a decision tree model that allows for customized prioritization based on the threat landscape and the organization’s specific needs.
To help organizations allocate resources effectively and address the most risky vulnerabilities, we have been publishing weekly blog posts since Week 32 of 2024 (end of July), highlighting the top 5 vulnerabilities each week. This prioritization is based on a decision-tree model trained on over 150,000 vulnerabilities. Approximately 25,170 vulnerabilities were published during this period, of which we have shortlisted 309. Follow our regular updates for more!