BUILDING DIGITAL RESILIENCE WITH AUTOMATION
Reduce noise. Uncover risks. Control your threat exposure with ENTRYZERO's AI wingman
Agentic AI Wingman
ENTRYZERO provides an always-on AI wingman to scale workforce in threat exposure management
- Visibility Hackers spot your weaknesses. Get their view of exposed IT assets, leaked credentials, and phishing bait
- Focus Hackers know which vulnerabilities matter. Do you? Use intel and real exploits to cut through the noise
- Readiness Outpace threat actors with an AI wingman orchestrating over 50 IT and security systems
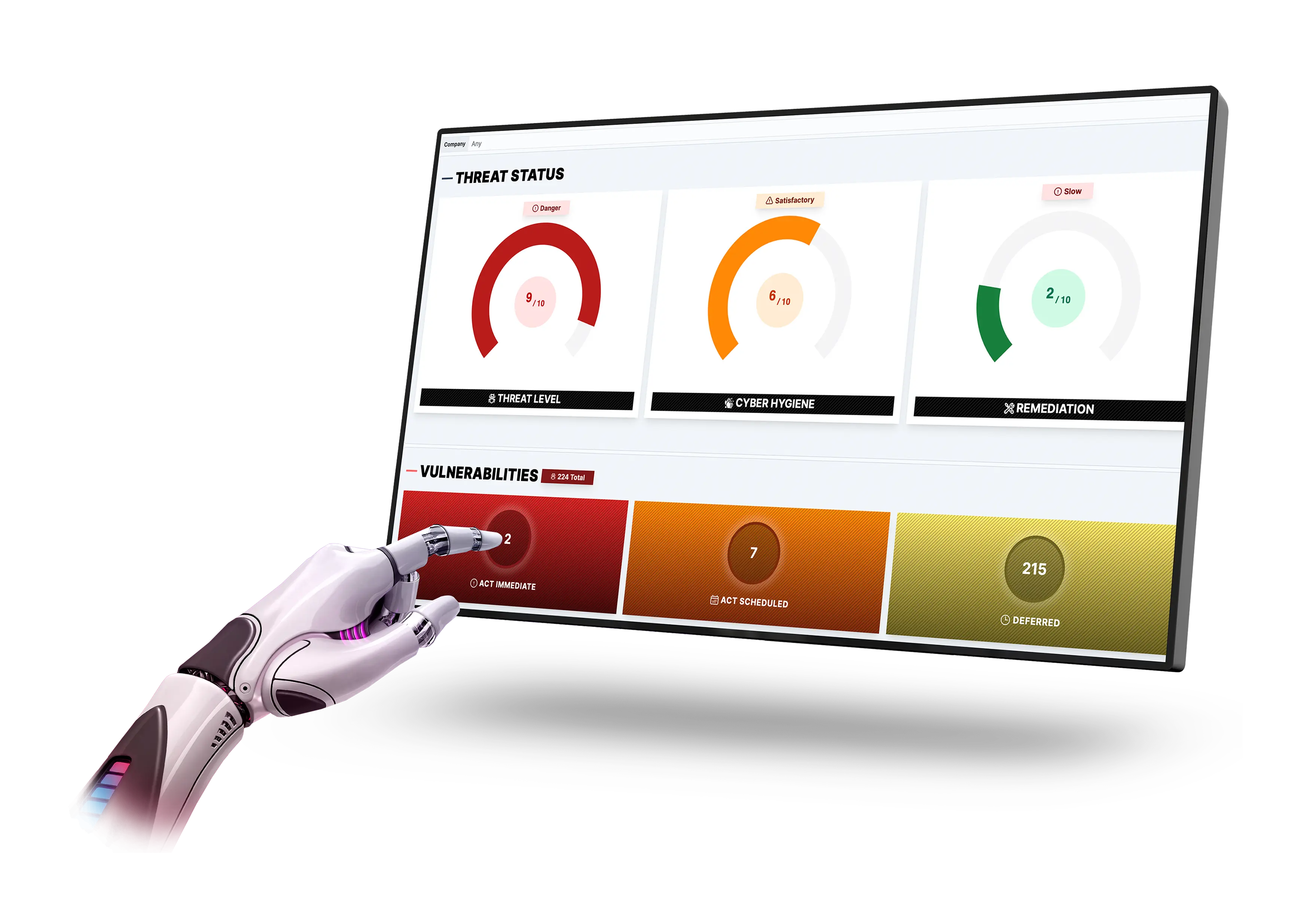
ENTRYZERO delivers continuous insights into threat exposure
Zero Input Discovery
Discovery of IT assets
AI-based validation
Software inventory
Exploitability Analysis
Threat intelligence
AI-powered shortlisting
Targeted exploitation
Daily Risk Assessment
Risk-based prioritization
Actionable recommendations
Proactive monitoring
ENTRYZERO fortifies digital resilience and optimizes resource use
Proactive Risk Reduction
With 94 % coverage of hacker-relevant vulnerabilities
Productivity boost
Scaled to 2+ full-time roles while accelerating results
Supply Chain Resilience
Neutralizing 82 % of supply chain risks before they strike
Use Cases
We collaborate with large businesses, the public sector, and researchers to reduce risk levels while conserving resources
Threat Exposure
Gain a continuous, comprehensive view of your cyber risks. ENTRYZERO delivers a prioritized assessment of threat exposure across your organization and subsidiaries through a hacker's perspective. Our AI wingman automatically maps offensive security steps to penetrate the perimeter. It performs a holistic inventory of IT assets, monitors dark web disclosures, and probes vulnerabilities for exploitability. Results are prioritized using ongoing threat analysis, empowering you to take proactive, informed action
Supply Chain
Your supply chain can put your business at risk. ENTRYZERO gives you complete visibility into cyber risks across your supplier ecosystem. Our AI wingman continuously monitor suppliers' exposed infrastructure, evaluates the effectiveness of their security controls, and supports remediation of critical issues - all in one platform. Proactively reduce the likelihood of breaches and strengthen the resilience of your supply chain to protect your business
SECURITY INSIGHTS
We constantly report on the latest developments in threat exposure management
Founding Team
Shape a trustworthy and lasting partnership with seasoned experts

Dr. Mohamad Sbeiti
Technical Lead
Led security consulting & attack surface evaluation for CARIAD, Volkswagen, T-Systems, & Deutsche Telekom; OSCE, OSCP, OSWP, CCSP

Samet Gökbayrak
Sales & Partnerships Lead
Managed international automotive clients at Deutsche Telekom, experienced in strategic programs with focus on sales & partnering
Contact Us
Reach out with the contact details below